Systemstandard
Ljus
Mörk

Författare
Anton Wadström
Read time
4 min
4 november 2022

On 2022-11-02, BleepingComputer reported that the Emotet malware operation came back to life after an almost four-month “vacation”.
In this blog post I’d like to suggest a few configuration changes you could implement in your organization to minimize your chances of being affected by the malware, as well as a few hunting queries for Microsoft Sentinel that could help you find Emotet exploitation attempts.
As seen in the BleepingComputer article, the macro enabled XLS-file contains instructions for the user on how to run the file.
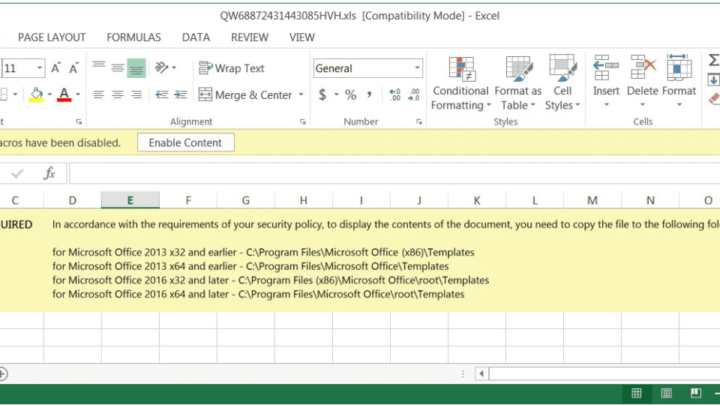
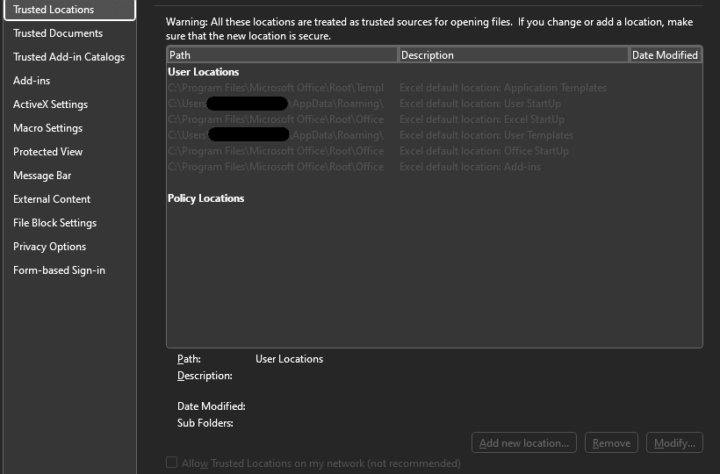
These instructions rely on a feature in Office called “Trusted locations”. Content, code, and add-ins are allowed to load from trusted locations with a minimal amount of security, without prompting the users for permission. If a dangerous file is opened from a trusted location, it will not be subject to standard security measures and could harm users’ computers or data.
To prevent these instructions from working if a user would follow them, we can disable trusted locations all together, or alter them to our desired configuration.
To see your own current configuration:
Here you’ll see all of your currently configured trusted locations. Note that there is a check box called “Disable all Trusted Locations”.
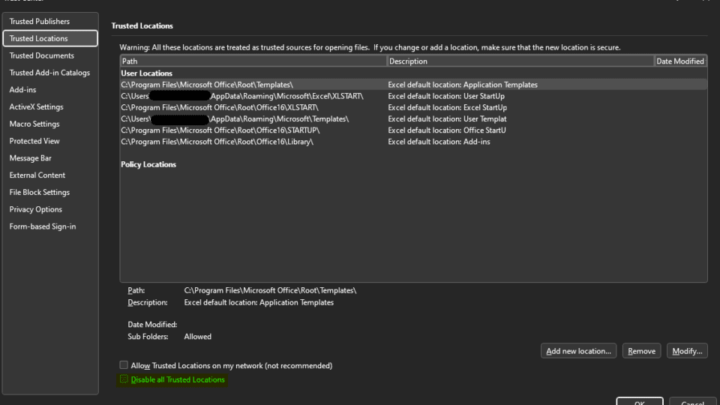
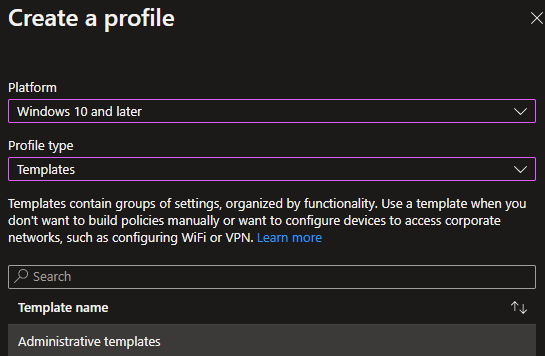
This check box is something we easily can configure with Group Policy, Configuration Manager, or Microsoft Intune. In this example we’ll use a configuration profile in Microsoft Intune to disable all trusted locations in all Office applications that support the option.
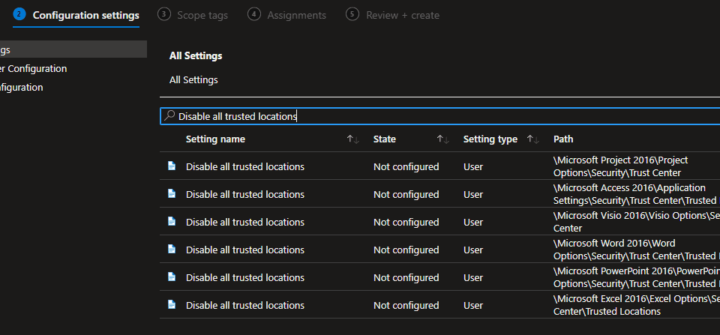

Optional: To add additional protection, you could disable the ability for users to enable content in macro enabled Office files – completely blocking macros to execute in files downloaded from the internet.
In the same configuration profile, search for ‘Block macros from running’ and enable each setting. Note that this might disrupt users that often work with macro enabled files that are shared from third parties.
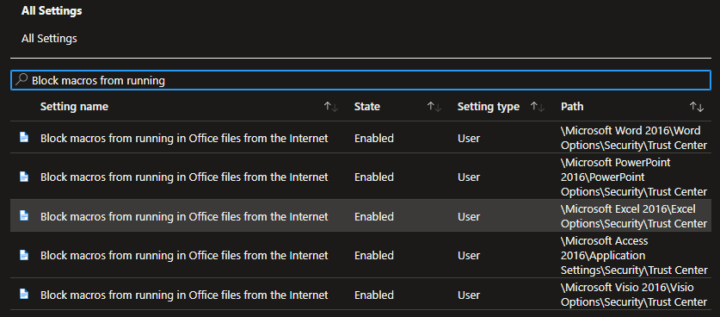
Once you’re happy with the configuration, assign the profile to the desired groups of users or devices and save it.
After a few minutes when the profile has synced to the target device(s). Opening Trust center in Excel once more shows that the settings have been applied:
With a configuration policy like this, your organization is better secured against attacks that utilize macro enabled Office documents in their modus operandi, not just Emotet.
The below queries as provided as-is with no guarantees that they will detect Emotet activity.
DLL created in %localappdata% and executed by Regsvr32.exe
When the macro runs, it will download a randomly named DLL file to a randomly named folder under %localappdata% (C:\\Users\\{username}\\AppData\\Local) and execute it with Regsvr32.exe.
This behavior can in theory be detected with the following KQL query in Microsoft Sentinel (requires Defender for Endpoint raw log ingestion), or in Defender for Endpoint Advanced Hunting. The query looks for events 7 days back but can be adjusted to your liking.
We can also use a list of known XLS file names (for example from Emotet samples uploaded to VirusTotal) and hunt for those in email attachments.
The following KQL query requires that Defender for Office raw logs are ingested to Sentinel.
By taking the NetworkMessageId from any results returned by the above query we can lookup the original email using the EmailEvents table:
This was a shorter blogpost on examples on how you can prevent and hunt for Emotet and other similar malware strains. As always, there are tons of additional actions you could take to better secure your organization against threats like these, and a thousand different detection mechanisms you could deploy.
It’s hard to fathom that we, in 2022, are still being affected by Office macros… Disable macro execution where you can and be done with it!
Vi har samlat några av branschens skickligaste molnkonsulter och tagit position som utmanare mot de traditionella drifts- och säkerhetsbolagen.
Oavsett var på er säkerhets- eller molnresa ni befinner er så kan vi hjälpa er att ta nästa steg. Med några av branschens allra skickligaste konsulter får ni det stöd ni behöver!