Ljus
Mörk
Författare
Anonym
SOC @ Asurgent
Read time
1 min
18 september 2023
Tomer Peled from Akamai explains that PowerShell can be made to run inside a pod. A pod is like a small computer space in Kubernetes. This is done by configuring something called 'volumes,' which are like shared folders.

YAML is a human-readable data serialization language that is often used for writing configuration files. Data serialization is a process of translating data structures and objects into a format that can be stored or transmitted.
YAML is widely used in Kubernetes and is a best practice to use in configuration generally.
Pods are the smallest deployable units of computing that you can create and manage in Kubernetes.
Tomer Peled from Akamai explains that PowerShell can be made to run inside a pod. A pod is like a small computer space in Kubernetes. This is done by configuring something called 'volumes,' which are like shared folders. To make this work you need to add a special instruction, called a 'volume parameter,' into a file written in a language called YAML. This file tells Kubernetes how to set up the pod.
Inside the YAML file, there is another setting called 'subPath.' This is where the problem lies. An attacker can use this 'subPath' setting to inject the PowerShell to do bad actions on the computer. Tomer Peled found that this 'subPath' was vulnerable to insecure function calls and a lack of user input sanitization.
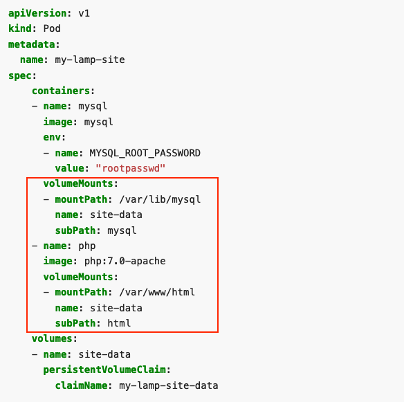
The attacker needs to have access to a node and ‘apply’ authorization. If the actor has permission listed communication can be achieved with the Kubernetes API on the target. The attacker can then inject arbitrary code for execution on the remote Windows endpoint.
Full walkthrough POC can be read at Can't Be Contained: Finding a Command Injection Vulnerability in Kubernetes | Akamai
To mitigate this issue, make sure that your Kubernetes version is above 1.28.
If this is not possible, the Kubernetes admin in your organization can disable the Volume.Subpath. This will prevent the CVE’s listed below from being exploited on your cluster.
Sources:
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-3676
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-3955
https://www.akamai.com/blog/security-research/kubernetes-critical-vulnerability-command-injection
Prenumerera på vårt nyhetsbrev för att ha koll på senaste nytt inom molnsfären.